
通过企业的专属云盘加密存储, 流-办公资料, 规避在Downloads, 分享文件, 或者通过微信, 钉钉, 邮箱等发送文件的过程中造成信息泄露.

涉密文档统一加密存储在企业云盘中, 而不存储在电脑, U 盘, 移动硬盘等固定设备中, 避免因设备丢失, 损毁或脱离管控而造成的资料泄密.

涉密文档存储在企业云盘中, 可以禁止拍照, 截屏, 复制, Downloads等操作行为, 杜绝文件信息泄露.

涉密文档 "只能用" "不能带走" , 规避离职人员在离职前有意获取, 带走重要文档而造成的信息泄露.
运用 360 FangCloud Enterprise Online Disk存储管理文档的企业, 可以通过本地加密, 文档内容管控, 离线文档管控等一系列能力, 保障从云端同步至本地的企业文档的安全.
办公场景
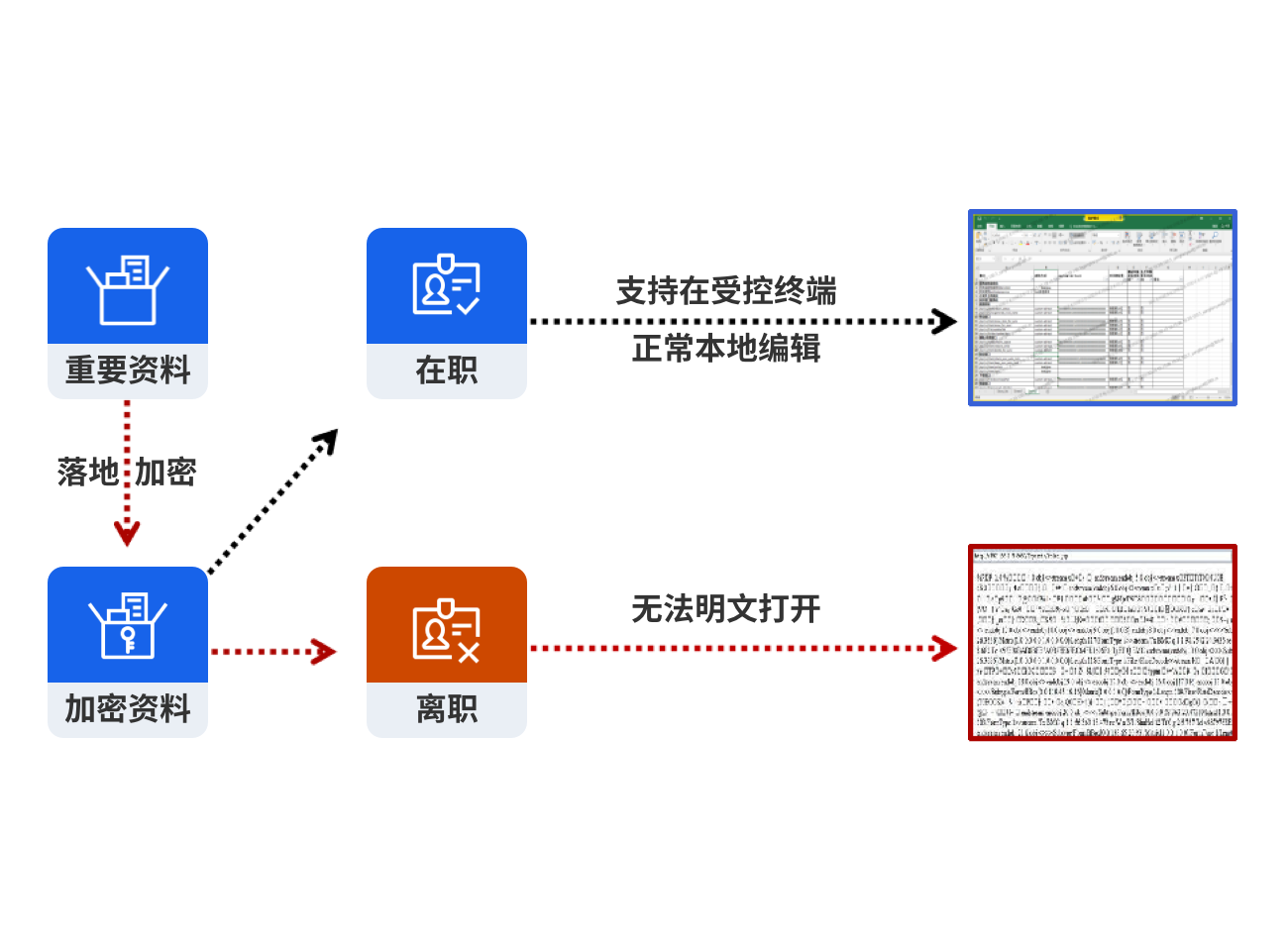
文档如果落到本地终端磁盘, 用户就可以随意通过微信, 钉钉, U 盘, 硬盘等拷贝, 流-, 造成文档泄漏. 尤其是员工离职前可能批量Downloads机密文档, 并带走谋取私利.
Solutions
存储在Fangcloud企业云盘上的机密文档一旦落地自动加密. 员工在职时, 可以通过受企业控制的终端设备 (如公司给员工配发的电脑) 查看, 编辑, 员工离职后用自己的电脑打开文件则为密文状态, 无法查看.
办公场景
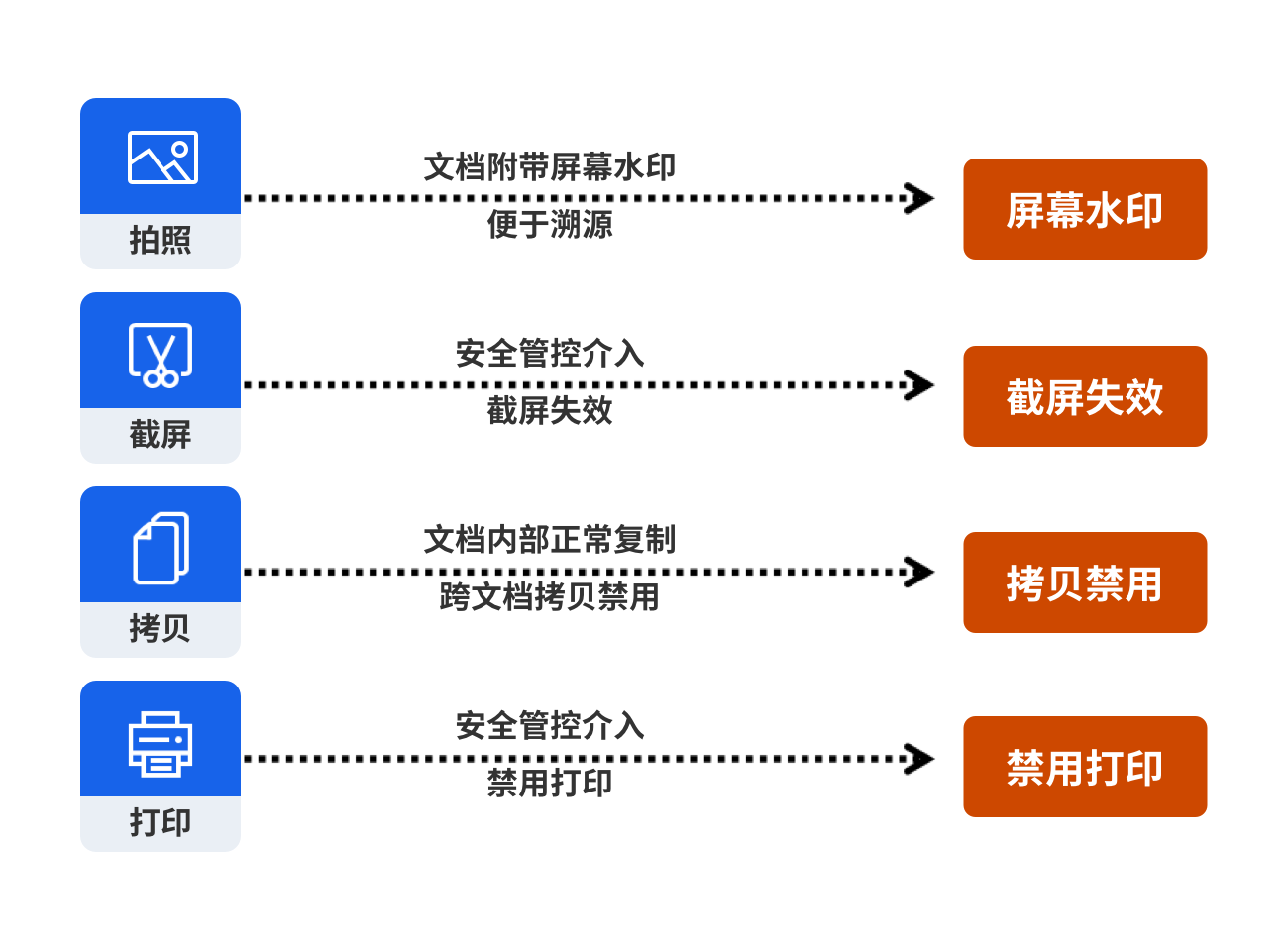
文档落到本地终端磁盘后, 针对文档内具体正文内容, 用户可以通过拍照, 录像, 截屏等方式获取, 且事后无法追溯审计, 造成信息泄露.
Solutions
员工在Fangcloud企业云盘上打开文件, 屏幕上会附带员工人水印, 对用户行为进行威慑, 也便于后期行为追溯; 可以对文档设置禁止截屏, 禁止打印, 只允许在本文档内进行复制, 禁止把 A 文档中的内容复制到 B 文档等.
办公场景
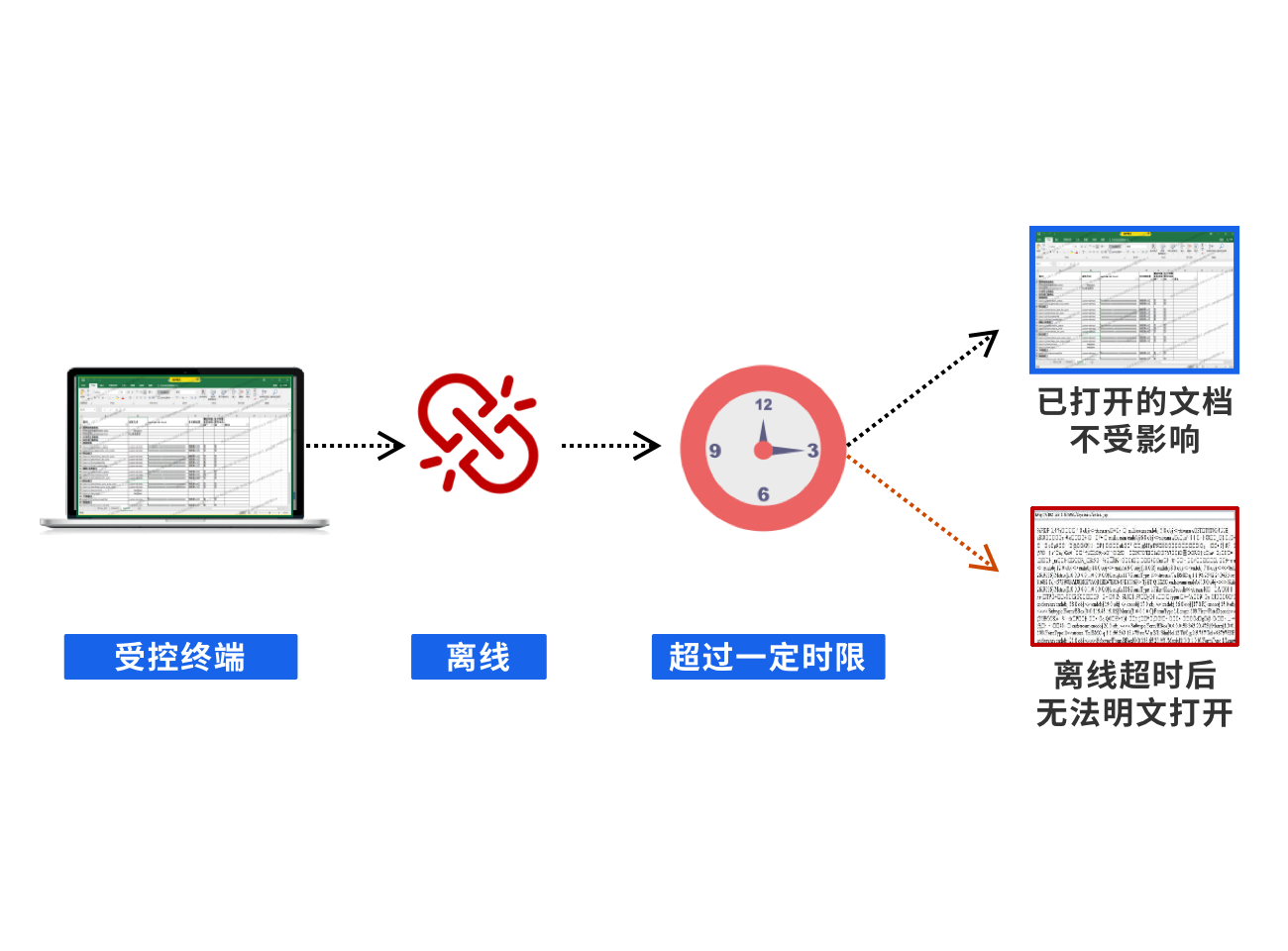
文档落到本地终端磁盘后, 如果工作人员意外将装有企业核心机密文档的电脑设备丢失了, 将很有可能导致设备中的落盘信息被泄漏.
Solutions
受公司网络控制的终端设备 (如公司给员工配备的办公电脑) 一旦脱离公司的网络, 且超过一定的时间, 落地至本地磁盘上的机密文档将无法明文打开, 无法被查看, 从而保障即使电脑丢失, 文档也不会泄露.
办公场景
文档如果落到本地终端磁盘, 用户就可以随意通过微信, 钉钉, U 盘, 硬盘等拷贝, 流-, 造成文档泄漏. 尤其是员工离职前可能批量Downloads机密文档, 并带走谋取私利.
Solutions
存储在Fangcloud企业云盘上的机密文档一旦落地自动加密. 员工在职时, 可以通过受企业控制的终端设备 (如公司给员工配发的电脑) 查看, 编辑, 员工离职后用自己的电脑打开文件则为密文状态, 无法查看.

办公场景
文档落到本地终端磁盘后, 针对文档内具体正文内容, 用户可以通过拍照, 录像, 截屏等方式获取, 且事后无法追溯审计, 造成信息泄露.
Solutions
员工在Fangcloud企业云盘上打开文件, 屏幕上会附带员工人水印, 对用户行为进行威慑, 也便于后期行为追溯; 可以对文档设置禁止截屏, 禁止打印, 只允许在本文档内进行复制, 禁止把 A 文档中的内容复制到 B 文档等.

办公场景
文档落到本地终端磁盘后, 如果工作人员意外将装有企业核心机密文档的电脑设备丢失了, 将很有可能导致设备中的落盘信息被泄漏.
Solutions
受公司网络控制的终端设备 (如公司给员工配备的办公电脑) 一旦脱离公司的网络, 且超过一定的时间, 落地至本地磁盘上的机密文档将无法明文打开, 无法被查看, 从而保障即使电脑丢失, 文档也不会泄露.

运用 360 FangCloud Enterprise Online Disk存储在云端的企业文档, 可以通过权限管理, 行为管控, 病毒防御, 存储备, 敏感词检测, 内容审计等一系列能力, 保障文档安全不泄露.
办公场景
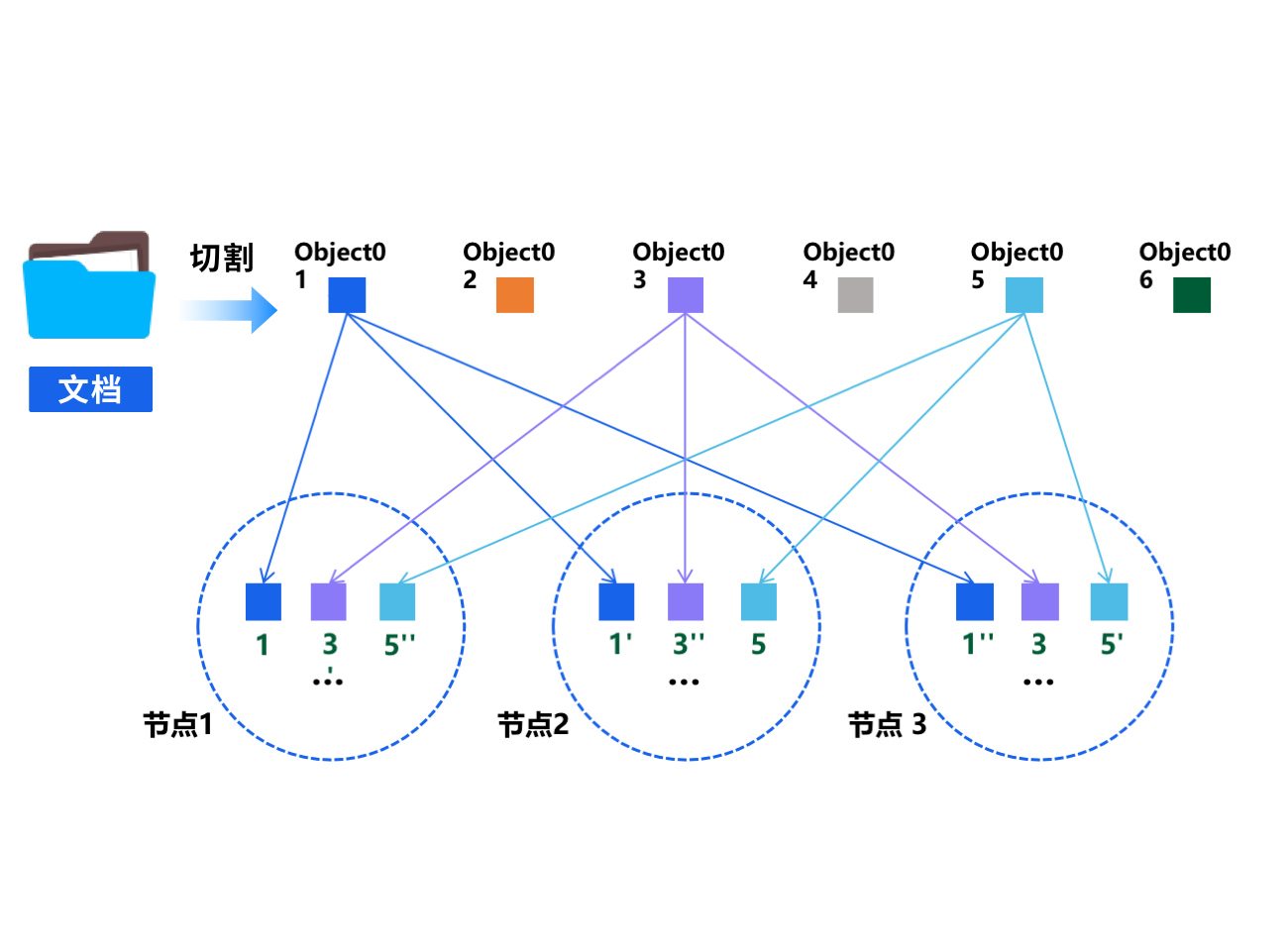
文件被员工不小心误删除或误修改, 上一版本的文件无法找回, 造成数据资产丢失.
Solutions
每文档被切分成大小一致的数据块, 数据块采用非明文加密算法处理, 采用三副本的存储方式, 均衡分布在系统各节点, 保障文档信息不丢失不泄露.
办公场景
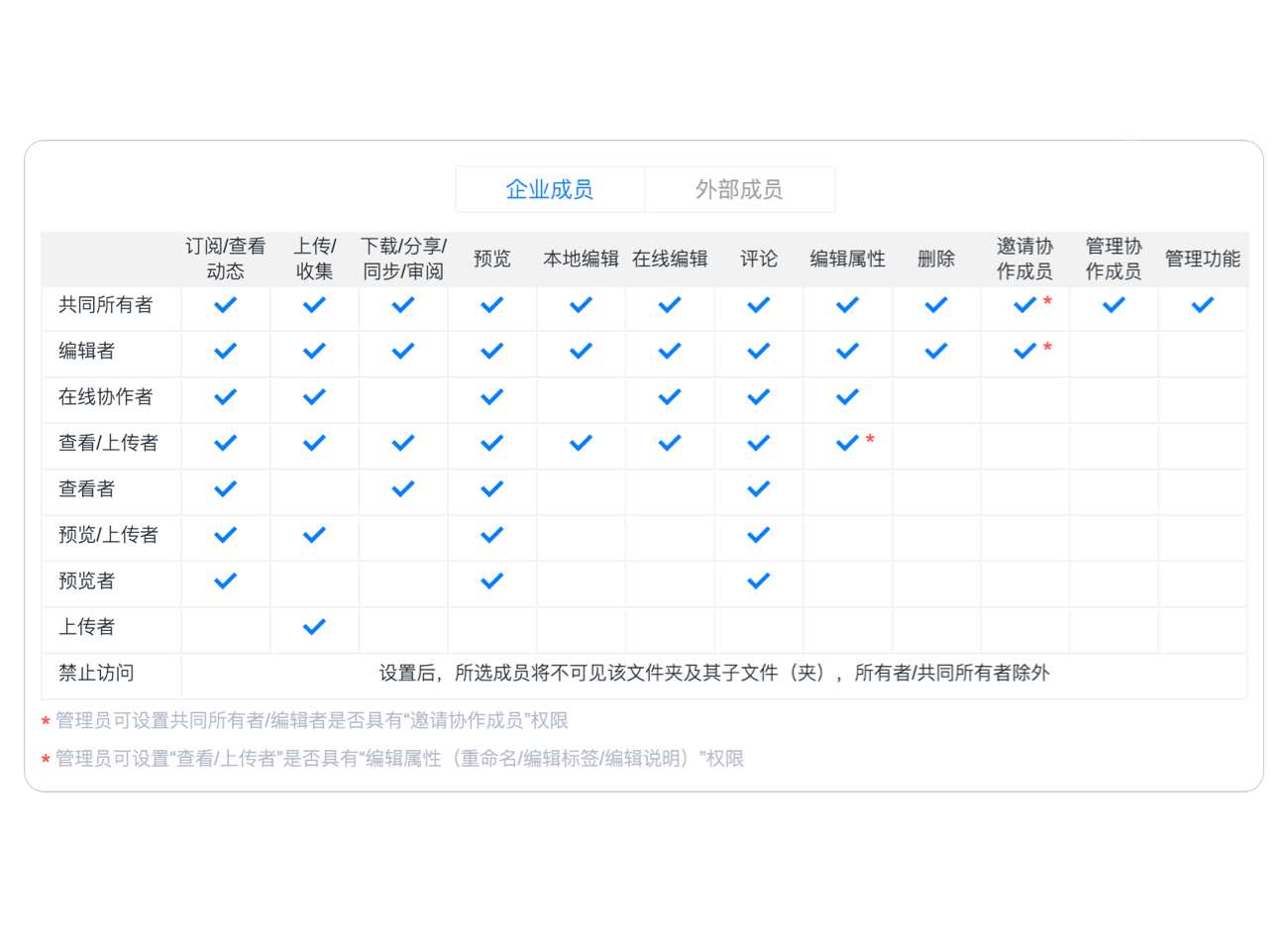
如果文档被不该查看, 操作的人预览, 编辑了, 可能会造成信息泄露, 此外也可能因为员工的误操作而造成文件丢失.
Solutions
系统对文档进行精细的权限管控, 不同的员工拥有不同的权限, 从而对员工上传, 预览, Downloads, 编辑, 移动, 分享文件的行为进行控制, 无权限者不得进行相关操作.

办公场景
用户对云端机密文档进行移动, 复制, 分享等敏感操作, 可能导致文档泄漏的风险.
解决方式
用户对云端受控文档进行敏感操作时, 将自动触发相关安全责任人的审批, 只有通过审批才能继续完成操作, 从而保障文档安全. 也可以周期性分析用户操作云盘文档的频率, 所操作文档的机要程度等, 识别用户的高风险行为, 并定期生成风险报告, 为企业文档安全管理提供风险预警.
办公场景
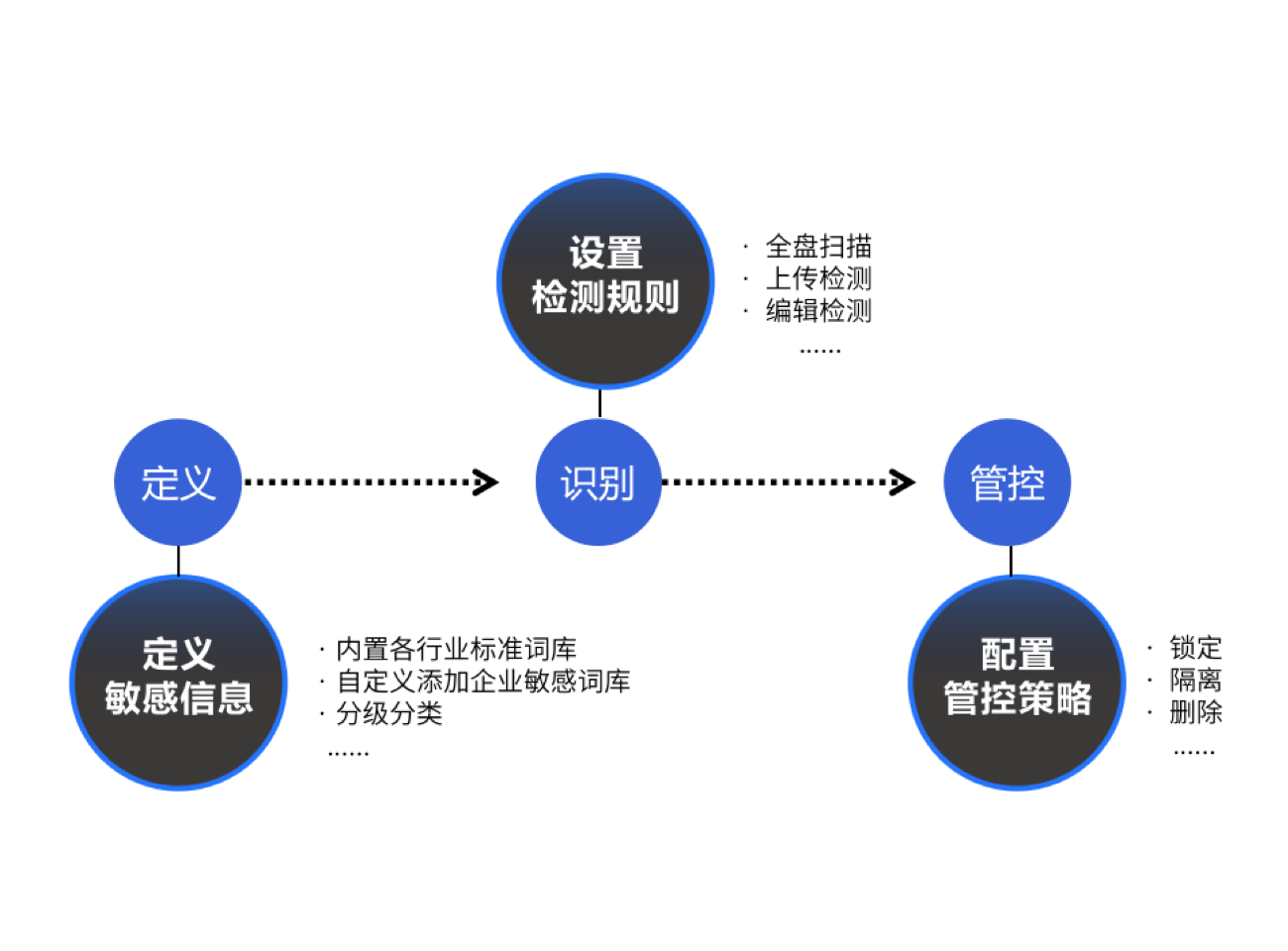
企业需要规避资料库中不合规文件, 敏感文件带来的审计和曝光风险, 因此需要及时把包含敏感内容的文件筛选出来.
解决方式
文件上传云盘时自动扫描, 用户也可以对整云盘进行内容识别, 发现敏感文件后进行隔离, 通知告警, 禁止分享Downloads等, 确保敏感信息不扩散.
办公场景
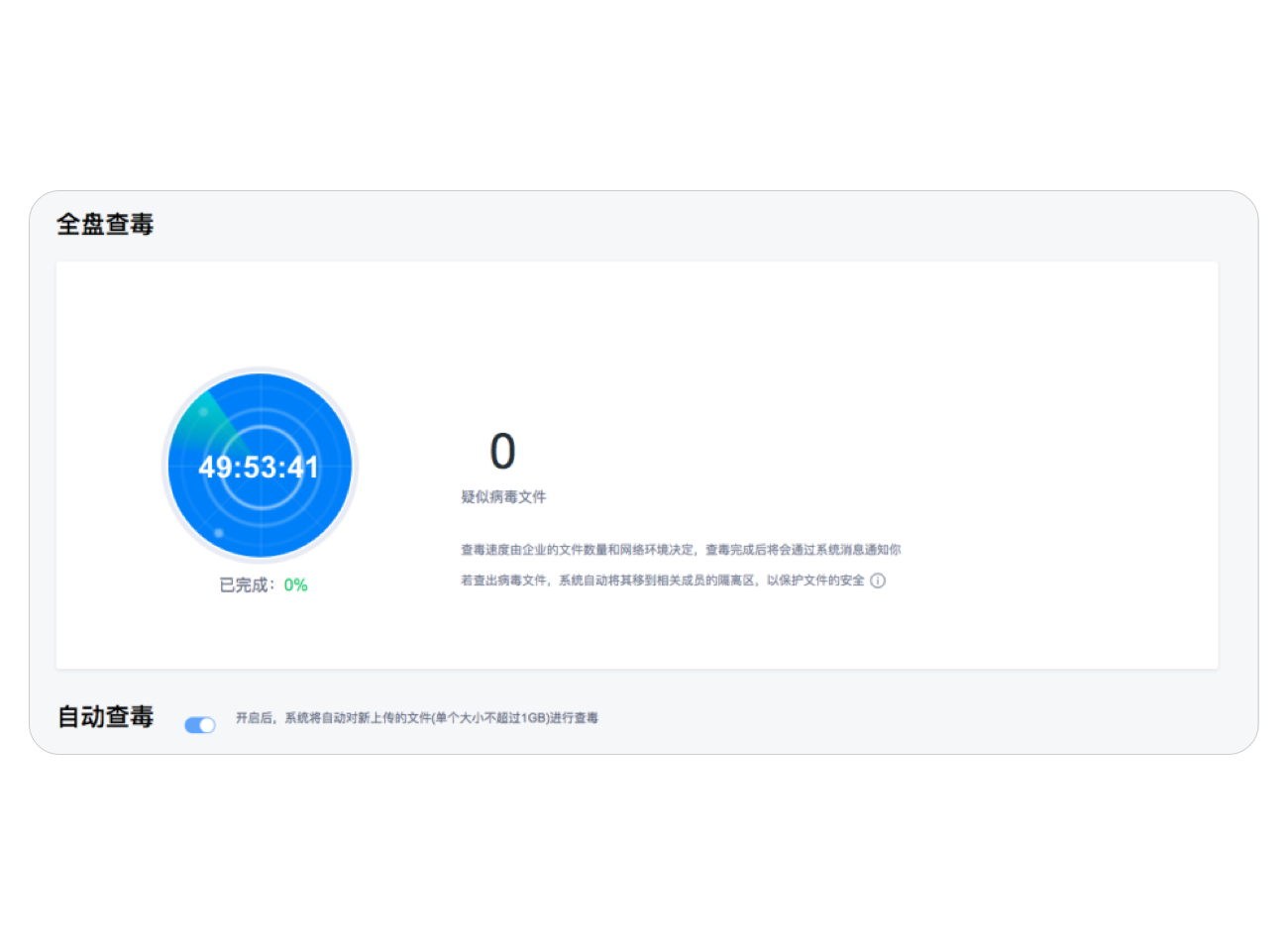
企业内部人员不小心 (或故意) 上传感染了病毒的文件到企业资料库中, 导致病毒文件扩散传播.
解决方式
开启 "自动查毒" 后, 系统会对上传 (增量) 文档进行自动查毒并标记正在查毒的状态; 用户可以在后台对全盘文件进行查毒. 查到病毒文档后, 系统会自动将病毒文档-移到隔离区, 并有消息提示, 避免其他文档被病毒污染.
办公场景
文件被员工不小心误删除或误修改, 上一版本的文件无法找回, 造成数据资产丢失.
Solutions
每文档被切分成大小一致的数据块, 数据块采用非明文加密算法处理, 采用三副本的存储方式, 均衡分布在系统各节点, 保障文档信息不丢失不泄露.

办公场景
如果文档被不该查看, 操作的人预览, 编辑了, 可能会造成信息泄露, 此外也可能因为员工的误操作而造成文件丢失.
Solutions
系统对文档进行精细的权限管控, 不同的员工拥有不同的权限, 从而对员工上传, 预览, Downloads, 编辑, 移动, 分享文件的行为进行控制, 无权限者不得进行相关操作.

办公场景
用户对云端机密文档进行移动, 复制, 分享等敏感操作, 可能导致文档泄漏的风险.
解决方式
用户对云端受控文档进行敏感操作时, 将自动触发相关安全责任人的审批, 只有通过审批才能继续完成操作, 从而保障文档安全. 也可以周期性分析用户操作云盘文档的频率, 所操作文档的机要程度等, 识别用户的高风险行为, 并定期生成风险报告, 为企业文档安全管理提供风险预警.

办公场景
企业需要规避资料库中不合规文件, 敏感文件带来的审计和曝光风险, 因此需要及时把包含敏感内容的文件筛选出来.
解决方式
文件上传云盘时自动扫描, 用户也可以对整云盘进行内容识别, 发现敏感文件后进行隔离, 通知告警, 禁止分享Downloads等, 确保敏感信息不扩散.

办公场景
企业内部人员不小心 (或故意) 上传感染了病毒的文件到企业资料库中, 导致病毒文件扩散传播.
解决方式
开启 "自动查毒" 后, 系统会对上传 (增量) 文档进行自动查毒并标记正在查毒的状态; 用户可以在后台对全盘文件进行查毒. 查到病毒文档后, 系统会自动将病毒文档-移到隔离区, 并有消息提示, 避免其他文档被病毒污染.

运用 360 FangCloud Enterprise Online Disk存储管理文档的企业, 可以针对文件内部分享/外部传送, 内外网文件交互等场景, 进行全面的文档安全防护.
办公场景
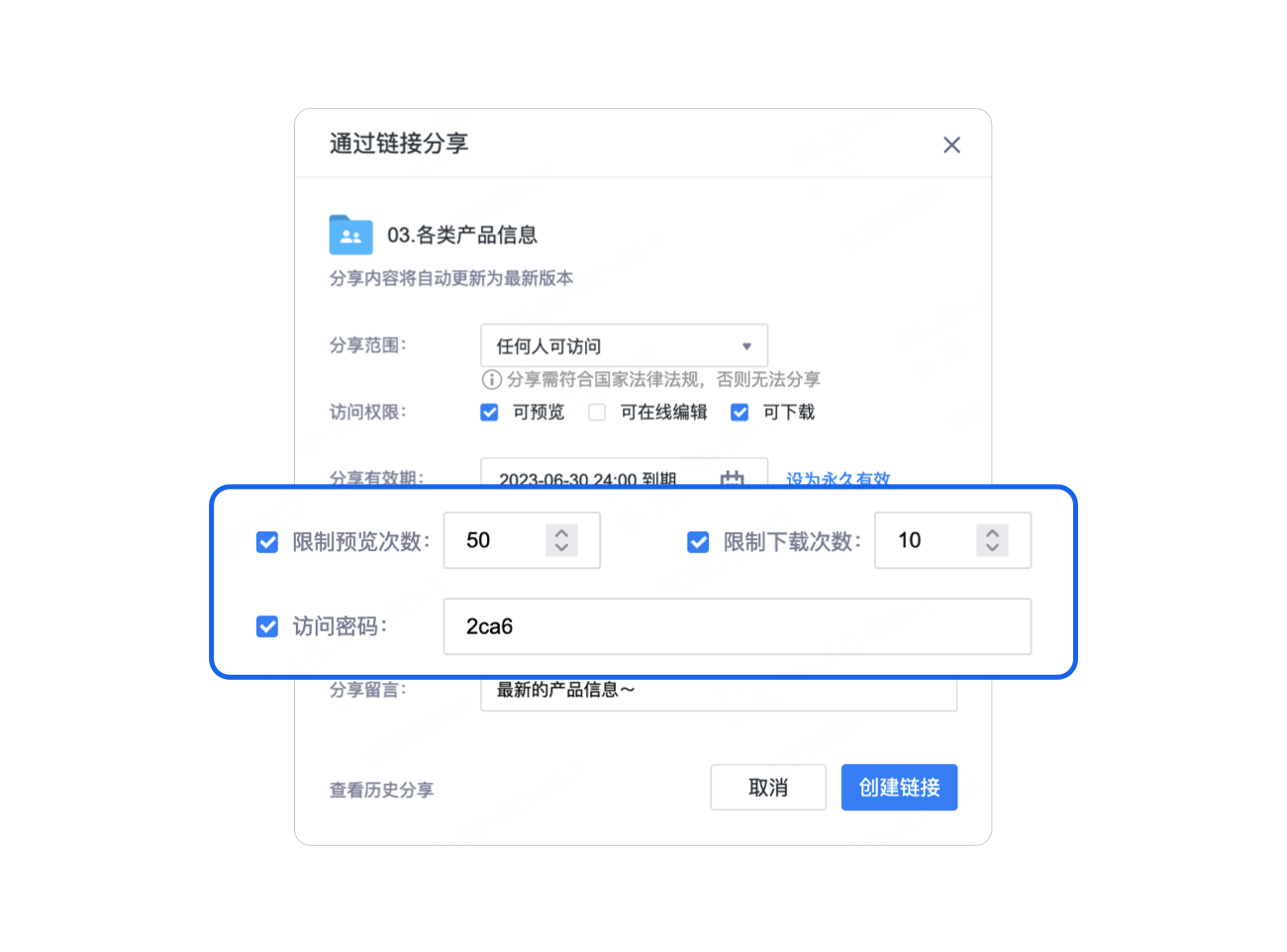
公司内部比较重要的资料, 在客户洽谈, 供应商合作等过程中, 不可避免地需要进行外发, 在此过程中就需要规避文件在外发, 使用过程中遭到泄露.
Solutions
在分享文档时, 可以设置分享文档允许被预览的次数, 允许被被Downloads的次数, 以及分享期限, 提取密码, 是否添加水印等.
办公场景
与客户, 供应商的合作中需要外发公司文件.
Solutions
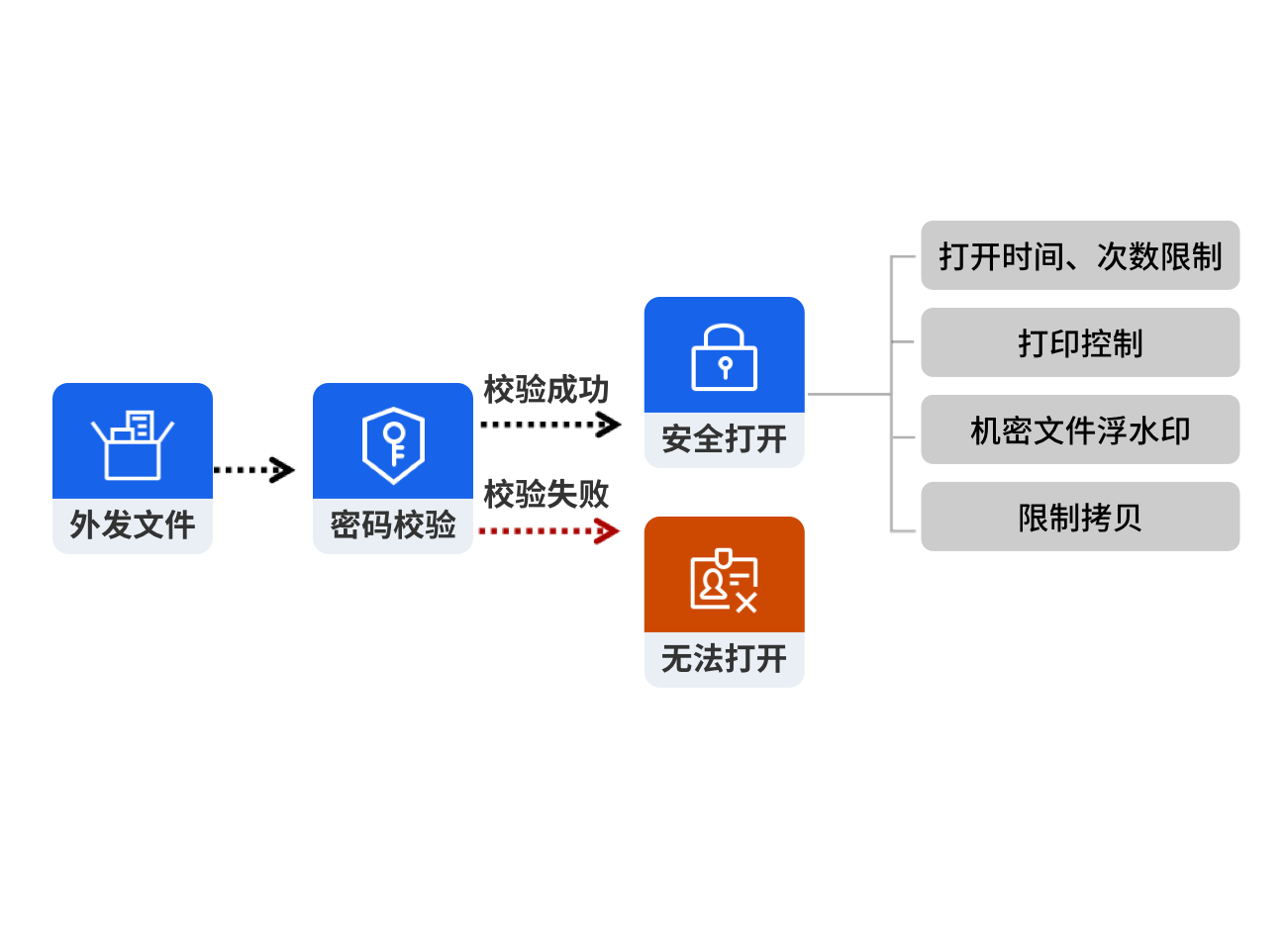
创建加密外发包与外部进行文档交互, 外部第三方客户需通过密码校验才能正常打开并使用外发包. 密文外发包具备防截屏, 防打印, 防复制功能, 且当打开次数耗尽或使用时间超限, 则外发文档自动销毁, 防止外发文档二次泄密.
办公场景
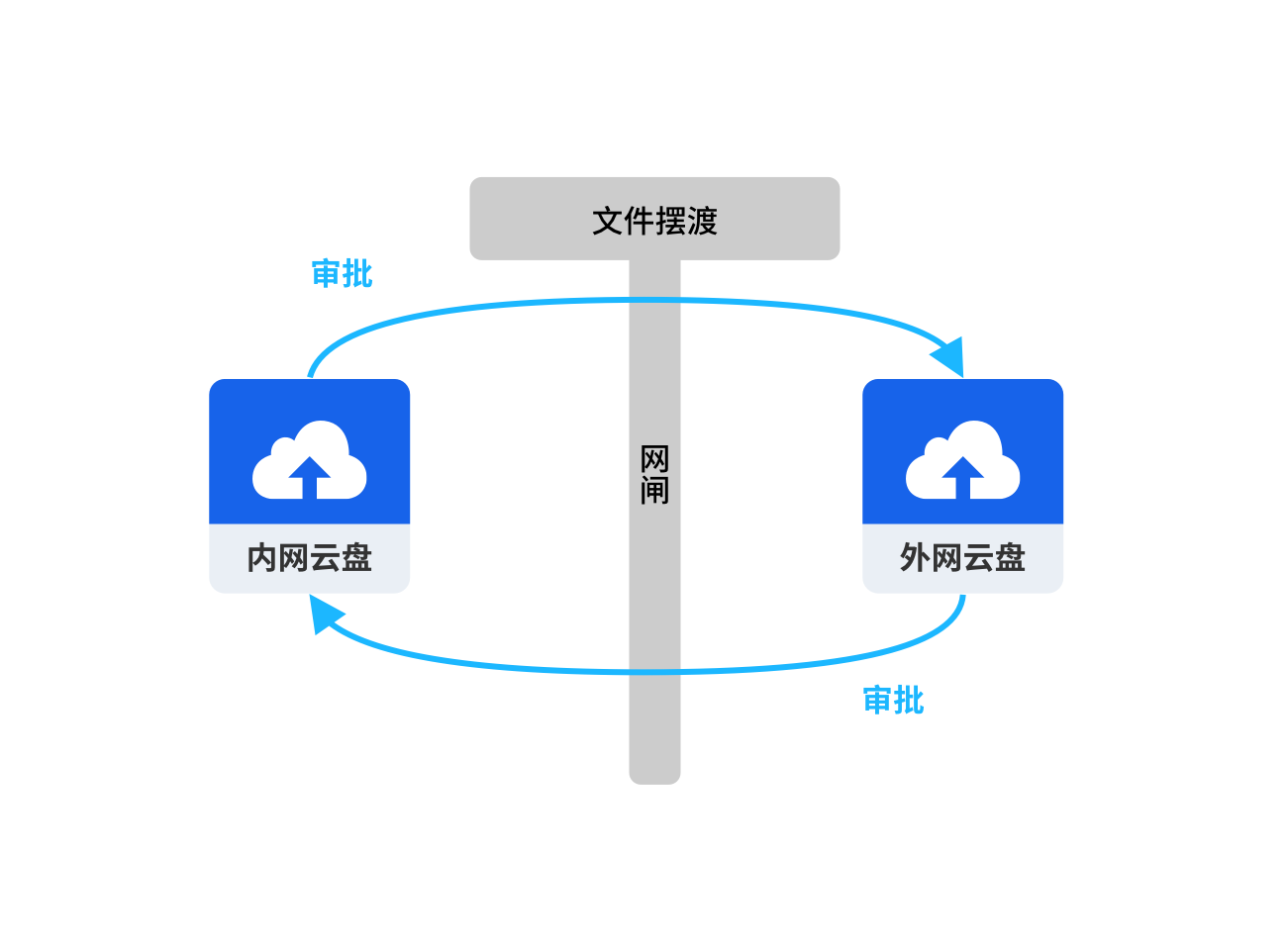
政务, 医疗, 科创实验室, 国企央企, 大型企业等拥有内网, 外网, 办公网, 研发网等多套网络系统, 为了保障数据安全, 相互之间进行了物理隔离, 文件跨网交换存在效率低, 流程繁杂, 审计难等困扰, 并存在合规风险.
Solutions
在多网络空间部署多套云盘, 通过云盘的网间摆渡系统实现安全, 合规, 便捷的跨网文件交换.
办公场景
公司内部比较重要的资料, 在客户洽谈, 供应商合作等过程中, 不可避免地需要进行外发, 在此过程中就需要规避文件在外发, 使用过程中遭到泄露.
Solutions
在分享文档时, 可以设置分享文档允许被预览的次数, 允许被被Downloads的次数, 以及分享期限, 提取密码, 是否添加水印等.

办公场景
与客户, 供应商的合作中需要外发公司文件.
Solutions
创建加密外发包与外部进行文档交互, 外部第三方客户需通过密码校验才能正常打开并使用外发包. 密文外发包具备防截屏, 防打印, 防复制功能, 且当打开次数耗尽或使用时间超限, 则外发文档自动销毁, 防止外发文档二次泄密.

办公场景
政务, 医疗, 科创实验室, 国企央企, 大型企业等拥有内网, 外网, 办公网, 研发网等多套网络系统, 为了保障数据安全, 相互之间进行了物理隔离, 文件跨网交换存在效率低, 流程繁杂, 审计难等困扰, 并存在合规风险.
Solutions
在多网络空间部署多套云盘, 通过云盘的网间摆渡系统实现安全, 合规, 便捷的跨网文件交换.
