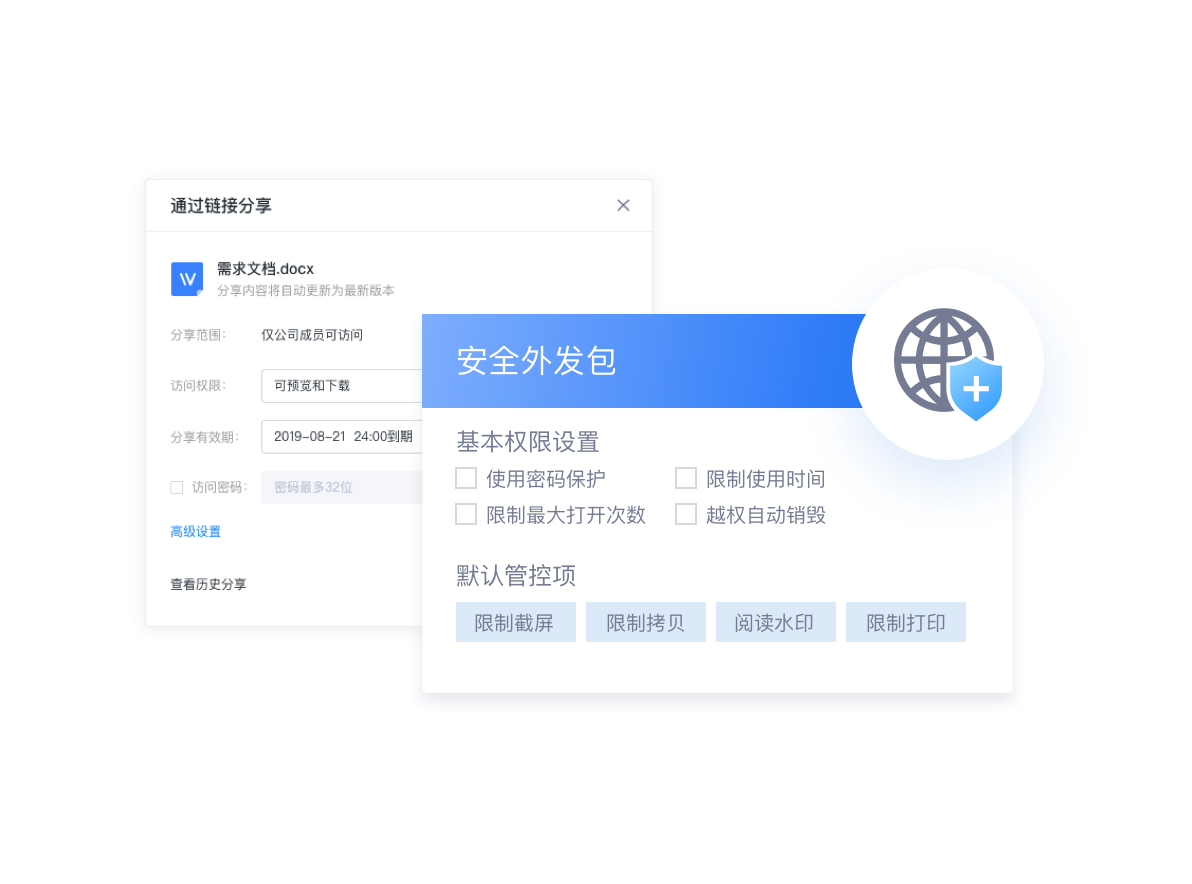
File storage and transmission control
Cloud control, Local control, Comprehensive combination of outsourcing management and control, Prevent losses caused by the leakage of important information of the enterprise.
Full link encrypted transmission
Cloud files are stored as ciphertext, upload, Downloads, Flow full link encryption.
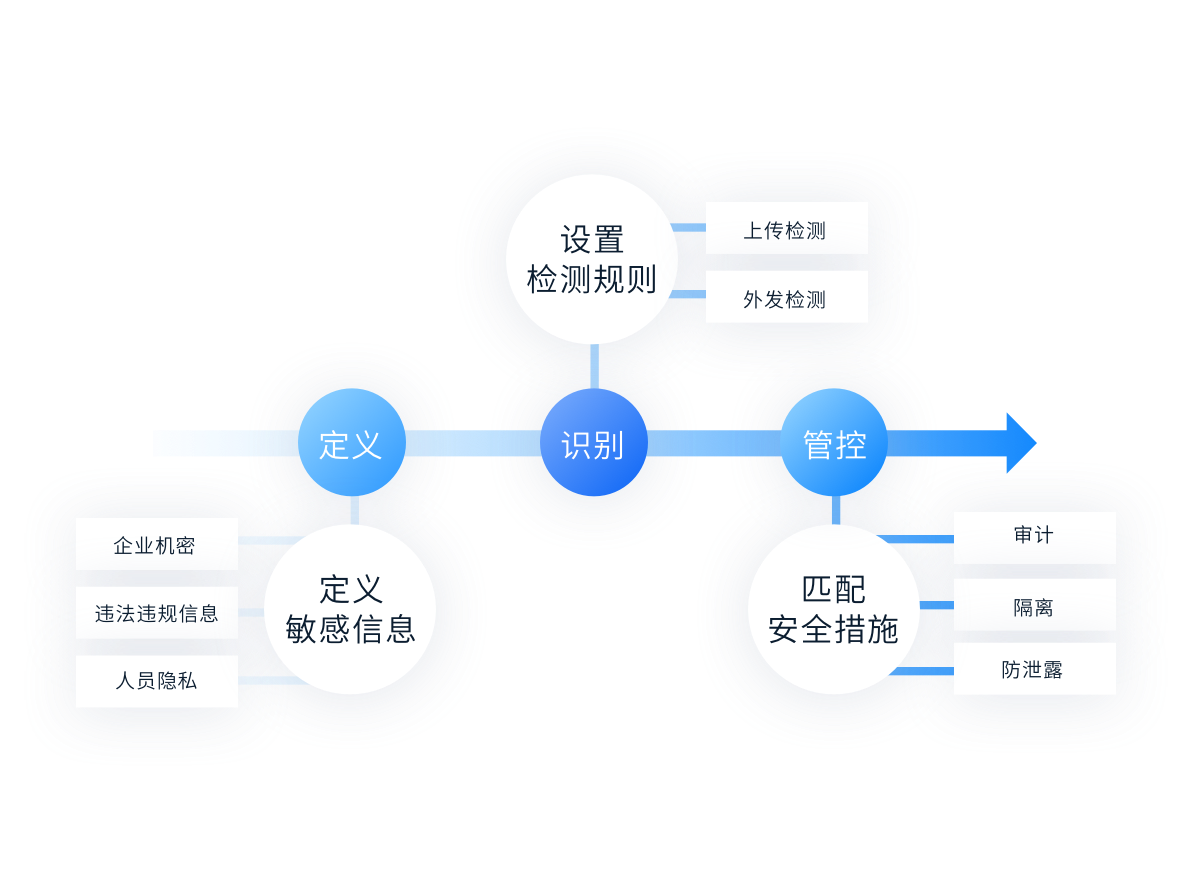
Important documents are not implemented
Important files are only allowed to be stored in the cloud, preview, edit, Prohibit downloading to PC End and mobile end, Avoid document leakage or damage through unsafe terminals.
Safety outsourcing
Select a file from the cloud disk/Folder to make outsourcing documents with specific permissions, When the outsourcing documents are shared/After downloading, Will be subject to security control, Include watermark, Anti copy, Anti printing, Limit open times/duration, Password protection, etc.

 400-993-9050
400-993-9050
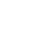






 浙公网安备 33011002015048 号
浙公网安备 33011002015048 号 Wechat Consulting
Wechat Consulting
 Phone consultation
Phone consultation