Online service
Phone consultation

Frequent data leakage events, Bringing various adverse impacts to the enterprise, The cost of data leakage is increasing.
Data has become one of the most valuable and vulnerable assets of enterprises, Protecting confidential data is crucial to any enterprise today.

Data protection laws and regulations have gradually emerged in China, Companies must keep up with policies, Violations can lead to reputational and financial risks.

Internal risks may bring greater harm, Adopting the right security policies and deploying anti leakage solutions can minimize it.

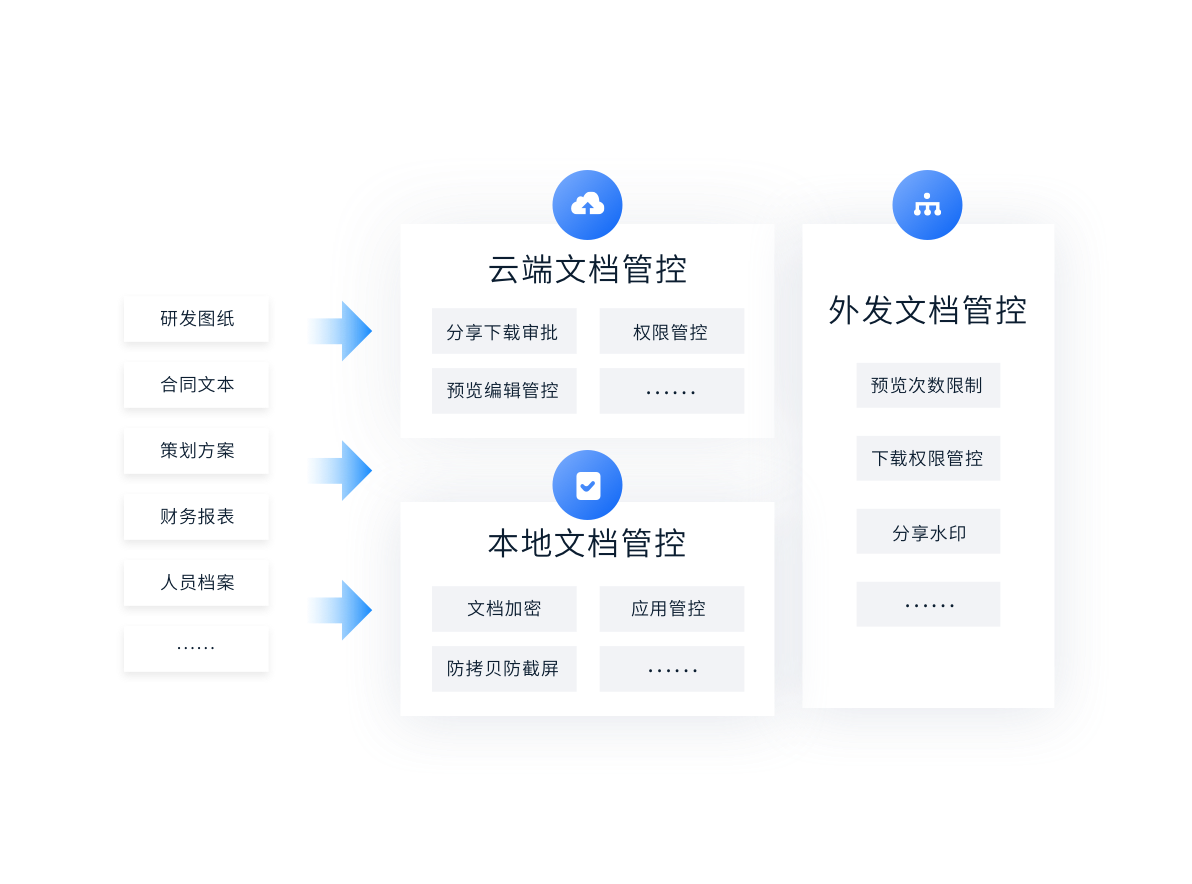
 Document leakage prevention
Document leakage prevention 
 Document not landing
Document not landing 
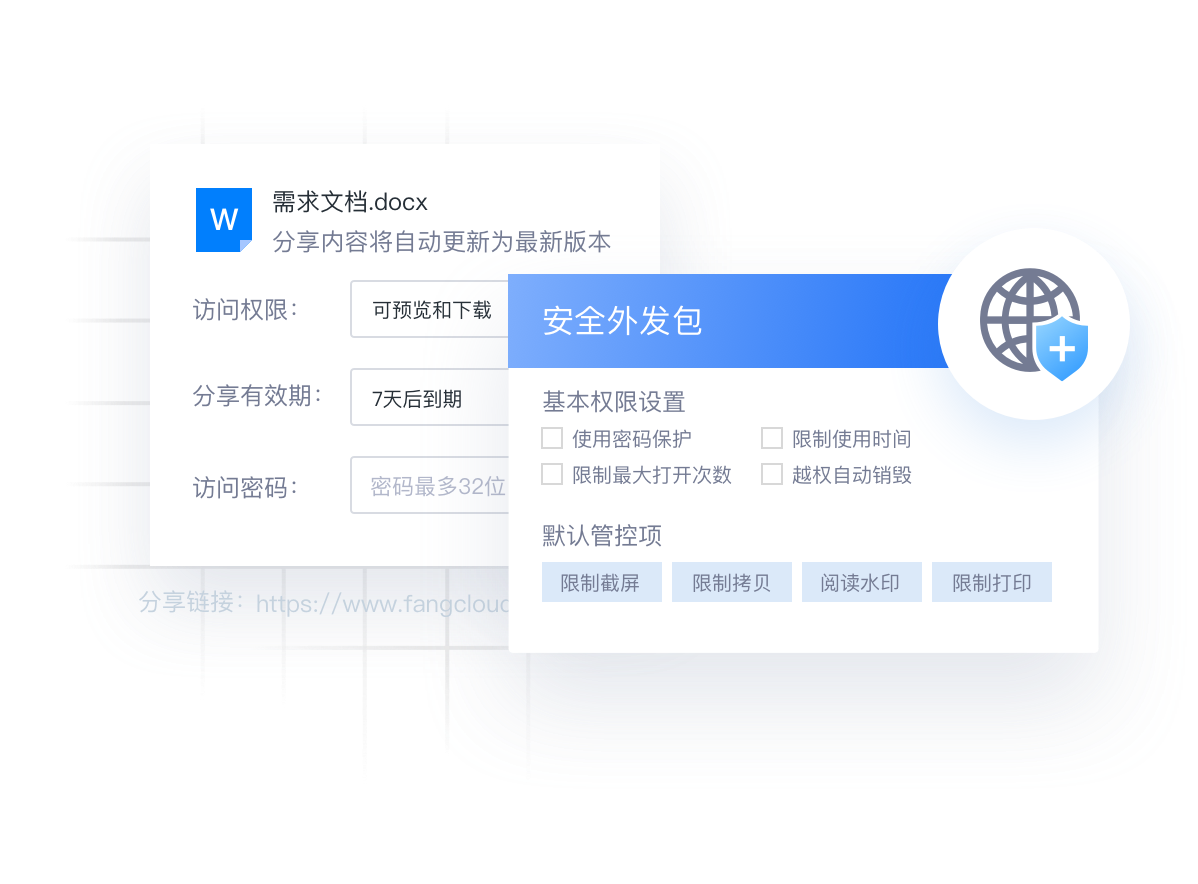
 Document security outgoing
Document security outgoing 
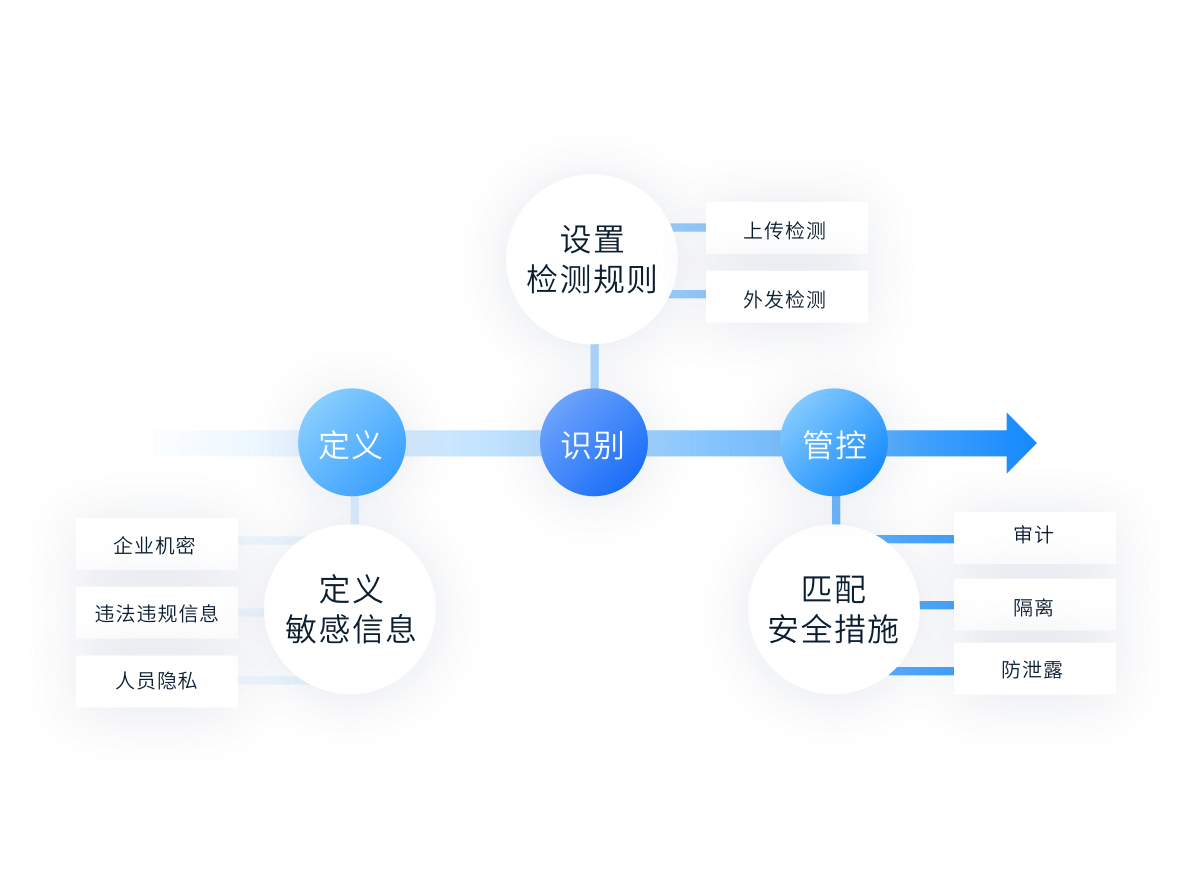
 Sensitive content identification
Sensitive content identification Document leakage prevention
Cloud control, Local control, Comprehensive integration of outsourcing control, Prevent losses caused by the leakage of important information of the enterprise.
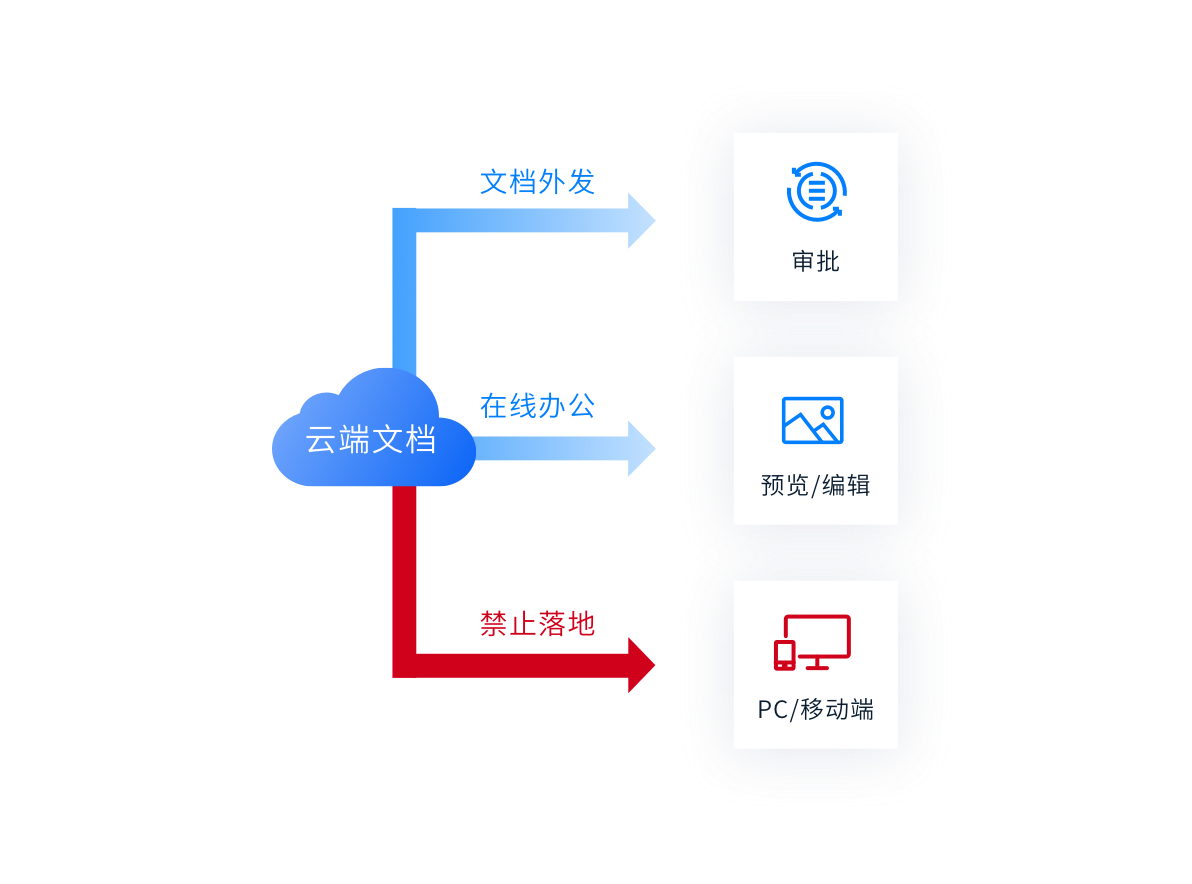
Document not landing
Important documents are stored in the cloud, While protecting security, Support cloud preview editing. Prevent documents from being leaked or damaged through insecure terminals.
Document security outgoing
Control and secure outsourcing through shared links, Make outgoing documents safe and controllable whether they are previewed online or viewed locally. Avoid external disclosure and secondary dissemination.
Sensitive content identification
Intelligent identification of document content according to detection rules, Audit or quarantine sensitive documents. Ensure enterprise document content compliance, Protect confidential enterprise information.
 Document leakage prevention
Document leakage prevention 
Document leakage prevention
Cloud control, Local control, Comprehensive integration of outsourcing control, Prevent losses caused by the leakage of important information of the enterprise.
 Document not landing
Document not landing 
Document not landing
Important documents are stored in the cloud, While protecting security, Support cloud preview editing. Prevent documents from being leaked or damaged through insecure terminals.
 Document security outgoing
Document security outgoing 
Document security outgoing
Control and secure outsourcing through shared links, Make outgoing documents safe and controllable whether they are previewed online or viewed locally. Avoid external disclosure and secondary dissemination.
 Sensitive content identification
Sensitive content identification 
Sensitive content identification
Intelligent identification of document content according to detection rules, Audit or quarantine sensitive documents. Ensure enterprise document content compliance, Protect confidential enterprise information.
An Internet Unicorn
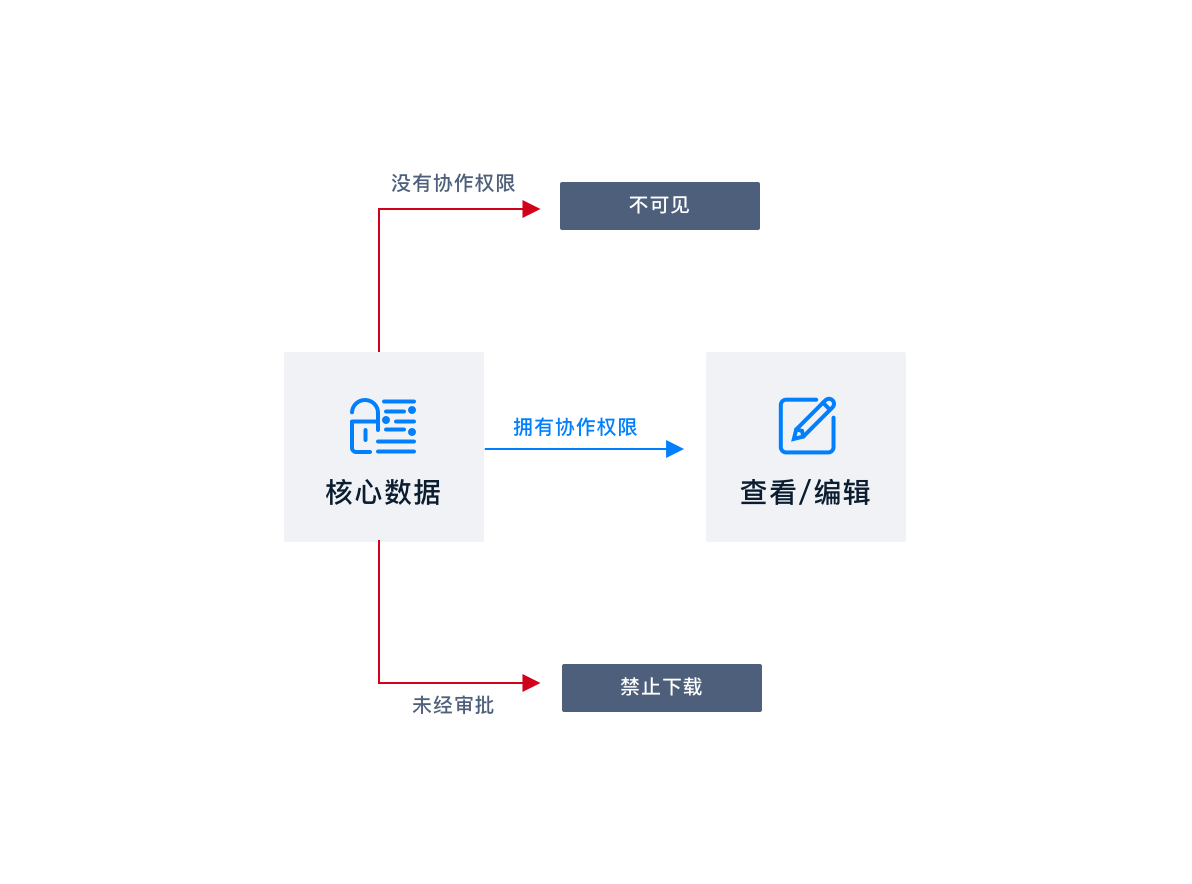
Core business data report archiving protection
Customer scenario:
Enterprise financial statements and business data reports need to be filed regularly and safely, Visible only to core personnel of the enterprise, Avoid leakage through various channels.
Solutions:
Through permission management, Only give the core personnel of the enterprise the right to cooperate. open "File not landing" after, Download and share reports, Approval required, Prohibit files from dropping to the local terminal at will. So as to ensure the safe archiving of reports in the cloud, Eliminate the risk of leakage from the terminal.
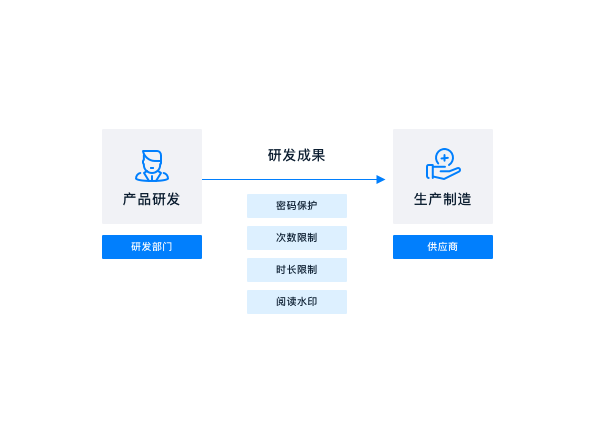
Research and Development Department of a high-end manufacturing enterprise
R & D drawings are safely shared with suppliers
Customer scenario:
Electronic drawings of enterprise core product parts, It needs to be sent to the supplier for production. Strictly limit the scope of use of drawings in suppliers, Prevent supplier proliferation.
Solutions:
Convert drawings into safe outgoing documents, Set the opening password, Open times, Security control of use duration and watermark. Ensure that the drawings are only available in a safe area.
Teaching and Research Department of an English Training School
Leakage prevention of teaching courseware
Customer scenario:
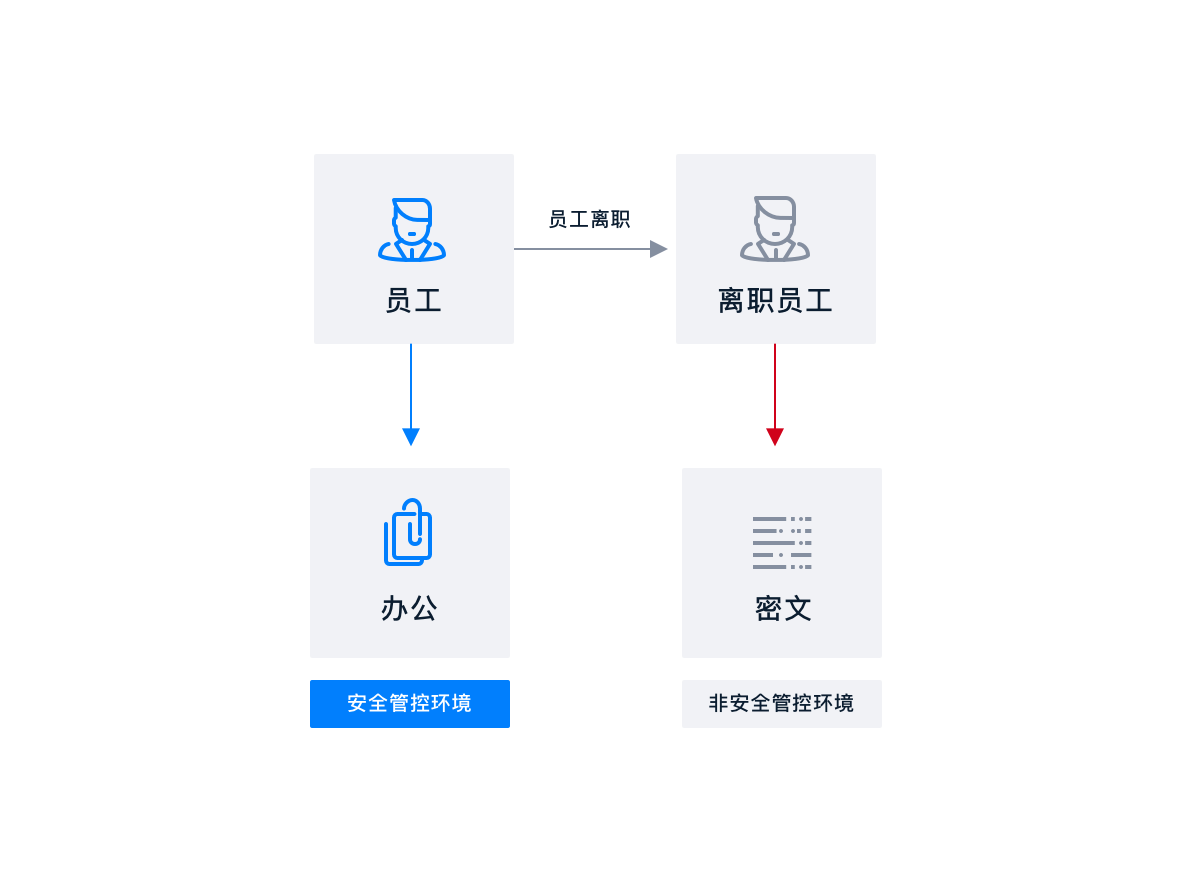
School teachers are highly mobile, Frequent job hopping among industries, Teaching courseware as the core asset of the school, Leakage after teachers leave, Cause losses to the school.
Solutions:
Teachers synchronize courseware materials to local, Automatic file encryption, Can work normally in a safe environment; The encrypted file on the computer cannot be opened after the teacher leaves.
Safe and efficient transfer to the office network, Assist in commercial promotion of achievements
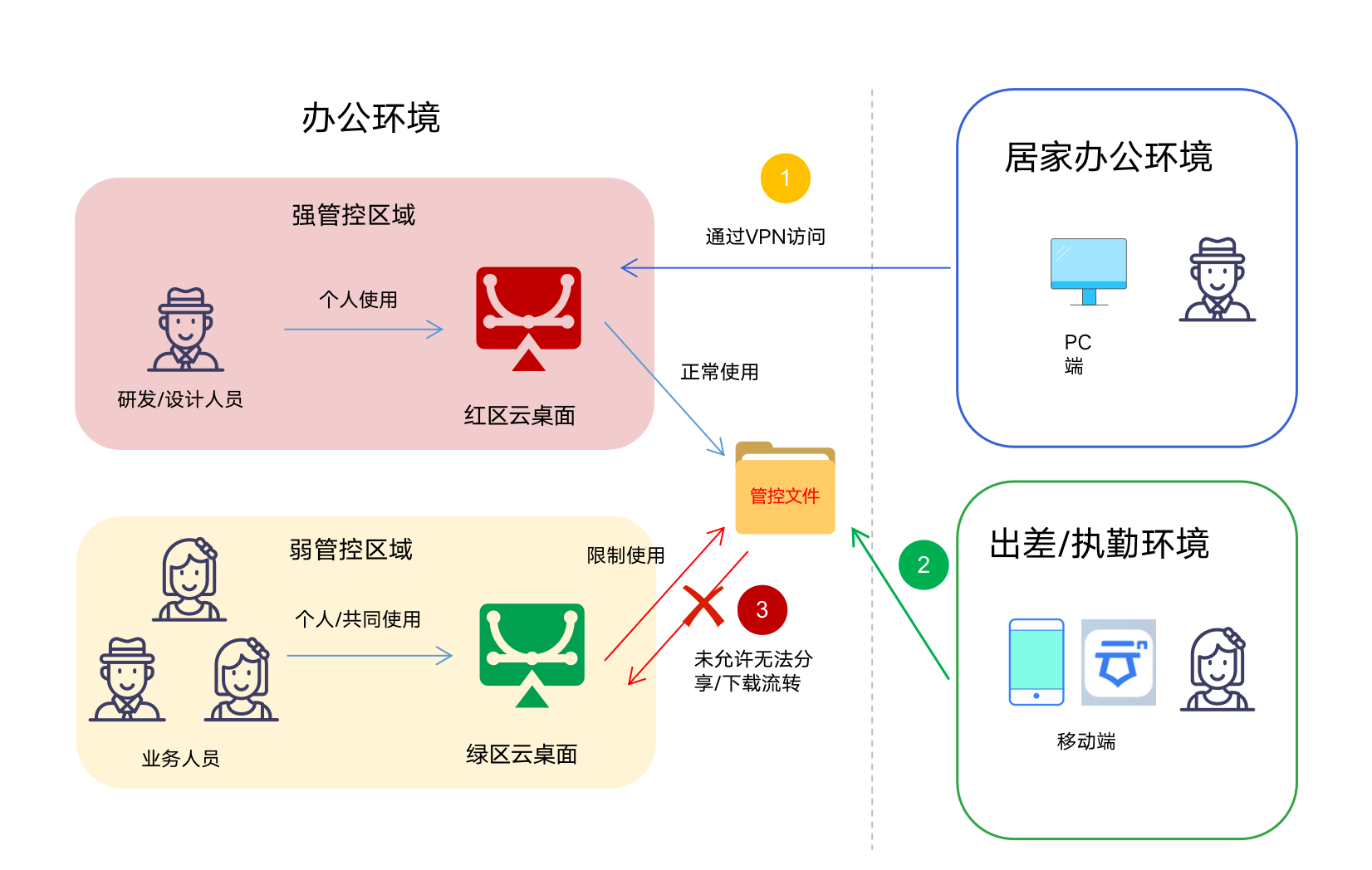
The customer has already launched a cloud desktop to protect documents from landing, Classified area (Red Zone Cloud Desktop) Core code generated in, Core assets such as scientific research achievements, Unable to securely transfer to non classified areas (Green Zone Cloud Desktop) , Facilitate market sales of scientific research achievements by laboratories, extension.

An Internet Unicorn
Core business data report archiving protection
Customer scenario:
Enterprise financial statements and business data reports need to be filed regularly and safely, Visible only to core personnel of the enterprise, Avoid leakage through various channels.
Solutions:
Through permission management, Only give the core personnel of the enterprise the right to cooperate. open "File not landing" after, Download and share reports, Approval required, Prohibit files from dropping to the local terminal at will. So as to ensure the safe archiving of reports in the cloud, Eliminate the risk of leakage from the terminal.

Research and Development Department of a high-end manufacturing enterprise
R & D drawings are safely shared with suppliers
Customer scenario:
Electronic drawings of enterprise core product parts, It needs to be sent to the supplier for production. Strictly limit the scope of use of drawings in suppliers, Prevent supplier proliferation.
Solutions:
Convert drawings into safe outgoing documents, Set the opening password, Open times, Security control of use duration and watermark. Ensure that the drawings are only available in a safe area.

Teaching and Research Department of an English Training School
Leakage prevention of teaching courseware
Customer scenario:
School teachers are highly mobile, Frequent job hopping among industries, Teaching courseware as the core asset of the school, Leakage after teachers leave, Cause losses to the school.
Solutions:
Teachers synchronize courseware materials to local, Automatic file encryption, Can work normally in a safe environment; The encrypted file on the computer cannot be opened after the teacher leaves.

Safe and efficient transfer to the office network, Assist in commercial promotion of achievements
The customer has already launched a cloud desktop to protect documents from landing, Classified area (Red Zone Cloud Desktop) Core code generated in, Core assets such as scientific research achievements, Unable to securely transfer to non classified areas (Green Zone Cloud Desktop) , Facilitate market sales of scientific research achievements by laboratories, extension.